January 7, 2026
By 2026, the promise of "Agentic AI" has fully materialized. We are no longer just asking LLMs to write summaries; we are deploying autonomous agents to manage our calendars, optimize cloud infrastructure, and even negotiate vendor contracts. These agents are, for all intents and purposes, your new digital employees.
However, with great power comes great vulnerability. LLM06: Excessive Agency has emerged as one of the most stealthy risks in the AI Security Framework. It occurs when we give our AI agents more functionality, more permissions, or more autonomy than they actually need to do their jobs.
Excessive agency isn't a single bug; it’s a design flaw that manifests in three specific ways:
An agent is given access to a "toolset" that is far too broad.
The agent is connected to downstream systems using a highly privileged service account.
SELECT user names, the underlying connection allows it to DROP tables or UPDATE credit balances if a prompt injection attack tricks it.The agent is allowed to execute high-impact actions without any human verification.
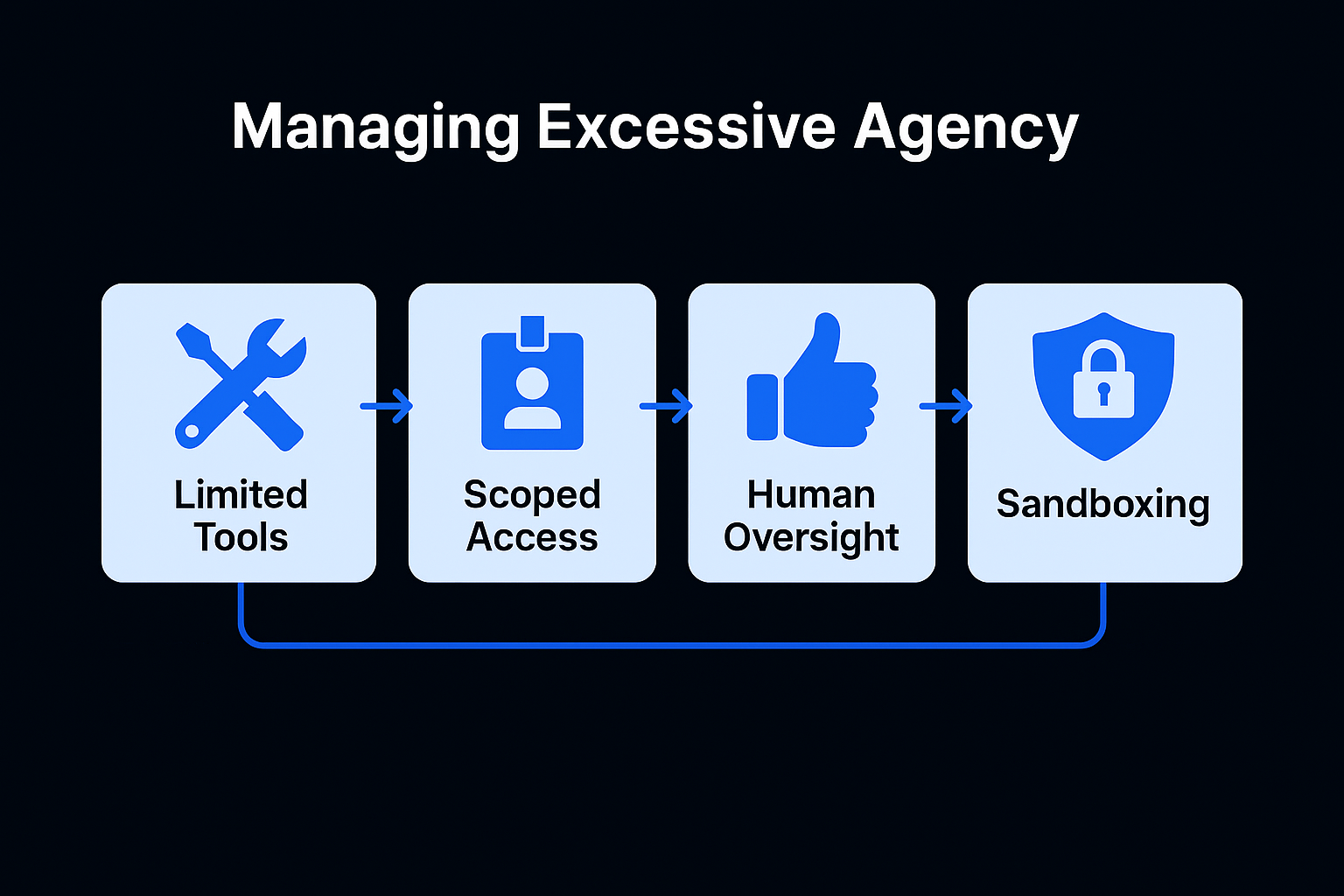
To secure the "action layer" of your AI, you must move away from general-purpose bots and toward Task-Specific Agents. Here is how to implement a zero-trust architecture for your AI workers.
Instead of giving an agent a "Shell Tool" (which can run any command), build specific, hardened functions for the exact tasks required.
execute_shell_command(cmd: string)get_server_uptime() or restart_service(service_name: "nginx")In 2026, every AI agent should have its own Non-Human Identity (NHI).
Certain actions are "too big to fail." Your architecture must include mandatory manual approvals for:
Run your agent's execution environment in a "sealed room." Use firewalled containers that have zero access to your internal network or sensitive configuration files (like .env or SSH keys) unless explicitly required for that specific turn.
Feature Appropriate Agency (Secure) Excessive Agency (Risky)
Tool Scope Granular (e.g., read_only_email) Broad (e.g., full_gmail_access)
Identity Session-bound, User-scoped Persistent "Admin" Service Account
Approval HITL for all "Write" actions Full autonomy for "Write" actions
Network Isolated Sandbox Full Internal Network Access
A new risk in 2026 is the rise of Shadow AI Agents. Employees are increasingly using unauthorized platforms (like personal Zapier or Make.com accounts) to build their own "work shortcuts." These agents often use broad OAuth grants to access corporate data.
Giving an AI agent "Admin" rights is the 2026 equivalent of leaving your master keys in the front door lock. To reap the benefits of automation without the catastrophic risks, you must build with Least Privilege at the core. Treat your agents as powerful tools that require constant, identity-based supervision.
Managing agency is a vital component of your overall AI Security Framework. Once you’ve mastered the permissions of your agents, the next challenge is ensuring the "instructions" they follow aren't being stolen—which leads us to the risk of System Prompt Leakage.